Digital twin consulting focuses on creating virtual replicas of physical assets and processes to optimize performance, predict maintenance needs, and enhance operational efficiency. Cybersecurity consulting centers on protecting digital assets by assessing vulnerabilities, implementing security protocols, and managing risk to prevent cyber threats. Explore how these specialized consulting services can transform your business's technological resilience and innovation strategies.
Why it is important
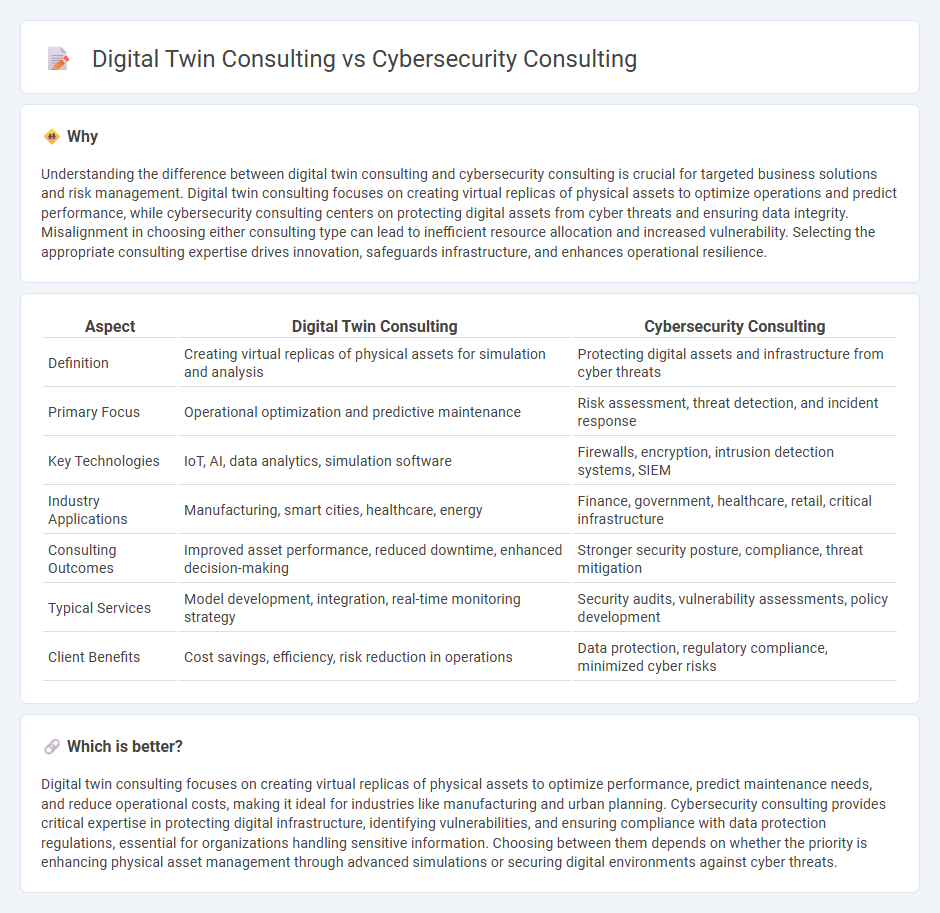
Understanding the difference between digital twin consulting and cybersecurity consulting is crucial for targeted business solutions and risk management. Digital twin consulting focuses on creating virtual replicas of physical assets to optimize operations and predict performance, while cybersecurity consulting centers on protecting digital assets from cyber threats and ensuring data integrity. Misalignment in choosing either consulting type can lead to inefficient resource allocation and increased vulnerability. Selecting the appropriate consulting expertise drives innovation, safeguards infrastructure, and enhances operational resilience.
Comparison Table
| Aspect | Digital Twin Consulting | Cybersecurity Consulting |
|---|---|---|
| Definition | Creating virtual replicas of physical assets for simulation and analysis | Protecting digital assets and infrastructure from cyber threats |
| Primary Focus | Operational optimization and predictive maintenance | Risk assessment, threat detection, and incident response |
| Key Technologies | IoT, AI, data analytics, simulation software | Firewalls, encryption, intrusion detection systems, SIEM |
| Industry Applications | Manufacturing, smart cities, healthcare, energy | Finance, government, healthcare, retail, critical infrastructure |
| Consulting Outcomes | Improved asset performance, reduced downtime, enhanced decision-making | Stronger security posture, compliance, threat mitigation |
| Typical Services | Model development, integration, real-time monitoring strategy | Security audits, vulnerability assessments, policy development |
| Client Benefits | Cost savings, efficiency, risk reduction in operations | Data protection, regulatory compliance, minimized cyber risks |
Which is better?
Digital twin consulting focuses on creating virtual replicas of physical assets to optimize performance, predict maintenance needs, and reduce operational costs, making it ideal for industries like manufacturing and urban planning. Cybersecurity consulting provides critical expertise in protecting digital infrastructure, identifying vulnerabilities, and ensuring compliance with data protection regulations, essential for organizations handling sensitive information. Choosing between them depends on whether the priority is enhancing physical asset management through advanced simulations or securing digital environments against cyber threats.
Connection
Digital twin consulting and cybersecurity consulting intersect through the need to protect the digital replicas of physical assets from cyber threats. Implementing robust cybersecurity measures ensures the integrity, confidentiality, and availability of data within digital twin systems used for real-time monitoring and predictive maintenance. Securing these environments mitigates risks associated with unauthorized access, data breaches, and operational disruptions in smart manufacturing, IoT, and industrial applications.
Key Terms
Risk Assessment
Cybersecurity consulting prioritizes risk assessment by identifying vulnerabilities in IT infrastructure, evaluating threats, and implementing defense mechanisms to protect data integrity and confidentiality. Digital twin consulting, on the other hand, utilizes real-time simulation models to predict operational risks, optimize system performance, and reduce failure probabilities in physical assets and processes. Discover how integrating these methodologies can enhance comprehensive risk management strategies.
Simulation Modeling
Cybersecurity consulting emphasizes protecting digital assets through risk assessment, threat detection, and compliance frameworks, ensuring robust defense against cyber attacks. Digital twin consulting centers on simulation modeling to create virtual replicas of physical systems, enabling performance optimization, predictive maintenance, and operational efficiency. Explore in-depth insights on how simulation modeling differentiates these consulting domains and drives innovation in your industry.
Incident Response
Cybersecurity consulting in incident response emphasizes rapid detection, containment, and mitigation of cyber threats to protect sensitive data and maintain system integrity. Digital twin consulting leverages virtual replicas of physical systems to simulate and analyze potential cyber-attacks, enabling proactive incident response planning and risk assessment. Explore the benefits of integrating these consulting approaches for enhanced organizational resilience.
Source and External Links
Cyber Security Consulting - IT Security Consulting | Risk Management - CyberSecOp offers tailored cybersecurity consulting services including risk assessment, program development, incident response, digital forensics, and virtual CISO support for various industries worldwide.
What Is a Cybersecurity Consultant? (And How to Become One) - Cybersecurity consultants identify risks, evaluate vulnerabilities, and implement solutions to protect organizations from cyber threats, requiring a blend of technical expertise and communication skills.
Cybersecurity Consulting Services - IBM - IBM provides industry-leading cybersecurity consulting, managed and cloud security services using AI-driven platforms to help organizations integrate security into their business transformation strategy effectively.
 dowidth.com
dowidth.com