AI readiness assessment consulting evaluates an organization's infrastructure, data capabilities, and talent to determine how well positioned it is to implement artificial intelligence solutions effectively. Cybersecurity consulting focuses on identifying vulnerabilities, protecting digital assets, and ensuring compliance with security regulations to safeguard an organization's information systems. Explore in-depth comparisons and benefits of each consulting type to optimize your business strategy.
Why it is important
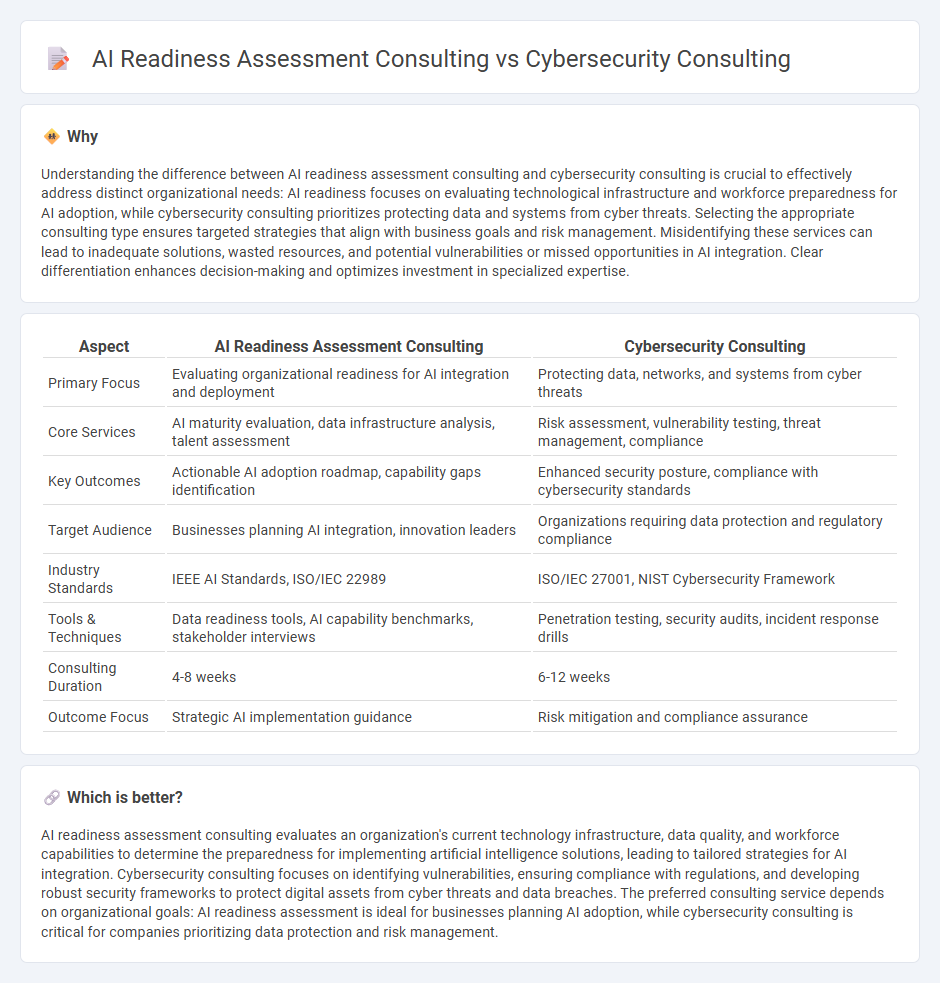
Understanding the difference between AI readiness assessment consulting and cybersecurity consulting is crucial to effectively address distinct organizational needs: AI readiness focuses on evaluating technological infrastructure and workforce preparedness for AI adoption, while cybersecurity consulting prioritizes protecting data and systems from cyber threats. Selecting the appropriate consulting type ensures targeted strategies that align with business goals and risk management. Misidentifying these services can lead to inadequate solutions, wasted resources, and potential vulnerabilities or missed opportunities in AI integration. Clear differentiation enhances decision-making and optimizes investment in specialized expertise.
Comparison Table
| Aspect | AI Readiness Assessment Consulting | Cybersecurity Consulting |
|---|---|---|
| Primary Focus | Evaluating organizational readiness for AI integration and deployment | Protecting data, networks, and systems from cyber threats |
| Core Services | AI maturity evaluation, data infrastructure analysis, talent assessment | Risk assessment, vulnerability testing, threat management, compliance |
| Key Outcomes | Actionable AI adoption roadmap, capability gaps identification | Enhanced security posture, compliance with cybersecurity standards |
| Target Audience | Businesses planning AI integration, innovation leaders | Organizations requiring data protection and regulatory compliance |
| Industry Standards | IEEE AI Standards, ISO/IEC 22989 | ISO/IEC 27001, NIST Cybersecurity Framework |
| Tools & Techniques | Data readiness tools, AI capability benchmarks, stakeholder interviews | Penetration testing, security audits, incident response drills |
| Consulting Duration | 4-8 weeks | 6-12 weeks |
| Outcome Focus | Strategic AI implementation guidance | Risk mitigation and compliance assurance |
Which is better?
AI readiness assessment consulting evaluates an organization's current technology infrastructure, data quality, and workforce capabilities to determine the preparedness for implementing artificial intelligence solutions, leading to tailored strategies for AI integration. Cybersecurity consulting focuses on identifying vulnerabilities, ensuring compliance with regulations, and developing robust security frameworks to protect digital assets from cyber threats and data breaches. The preferred consulting service depends on organizational goals: AI readiness assessment is ideal for businesses planning AI adoption, while cybersecurity consulting is critical for companies prioritizing data protection and risk management.
Connection
AI readiness assessment consulting identifies an organization's capacity to implement AI technologies securely, highlighting potential vulnerabilities and compliance gaps. Cybersecurity consulting addresses these vulnerabilities by designing robust protection strategies to safeguard sensitive data and AI infrastructure. Together, they ensure a secure and efficient AI adoption roadmap aligned with regulatory standards and risk management.
Key Terms
Risk Assessment
Cybersecurity consulting primarily involves evaluating vulnerabilities and threat landscapes to implement robust defense mechanisms against data breaches, malware, and cyberattacks. AI readiness assessment consulting focuses on identifying risks related to AI deployment, including ethical concerns, bias mitigation, and compliance with regulatory standards. Discover how tailored risk assessments in both fields can protect your organization by exploring comprehensive consulting strategies.
Compliance Auditing
Cybersecurity consulting emphasizes compliance auditing to ensure organizational adherence to regulations like GDPR, HIPAA, and PCI-DSS by identifying vulnerabilities and implementing risk mitigation strategies. In contrast, AI readiness assessment consulting evaluates the preparedness of AI systems and processes for regulatory compliance, focusing on data privacy, ethical AI use, and algorithmic transparency. Explore further to understand how tailored compliance auditing drives both cybersecurity resilience and responsible AI deployment.
Data Governance
Cybersecurity consulting primarily addresses protecting data integrity, confidentiality, and availability through risk assessments, threat analysis, and compliance with regulations like GDPR and HIPAA, ensuring robust data governance frameworks. AI readiness assessment consulting evaluates an organization's infrastructure, data quality, and governance policies to determine preparedness for implementing AI technologies while safeguarding ethical data use and compliance with AI-specific standards. Explore comprehensive strategies to align cybersecurity and AI data governance efforts effectively.
Source and External Links
Cyber Security Consulting - IT Security Consulting | Risk Management - CyberSecOp delivers strategic cybersecurity consulting, incident response, risk management, and compliance services tailored for organizations across multiple industries worldwide.
Top 10 cyber consultants - Cyber Magazine highlights leading global consulting firms like Infosys Consulting, which specialize in evaluating security vulnerabilities, developing defensive strategies, and helping businesses maintain strong cyber defenses.
What Is a Cybersecurity Consultant? (And How to Become One) - Cybersecurity consultants assess risks, implement protective measures, and provide solutions to safeguard companies' networks and data from evolving cyber threats.
 dowidth.com
dowidth.com