Data clean rooms enable multiple parties to securely collaborate on aggregated data without exposing individual-level information, ensuring privacy compliance and reducing data leakage risks. Secure enclaves provide isolated, encrypted computing environments that protect sensitive data during processing, guarding against unauthorized access and tampering. Explore how these technologies transform secure data collaboration and privacy standards in modern commerce.
Why it is important
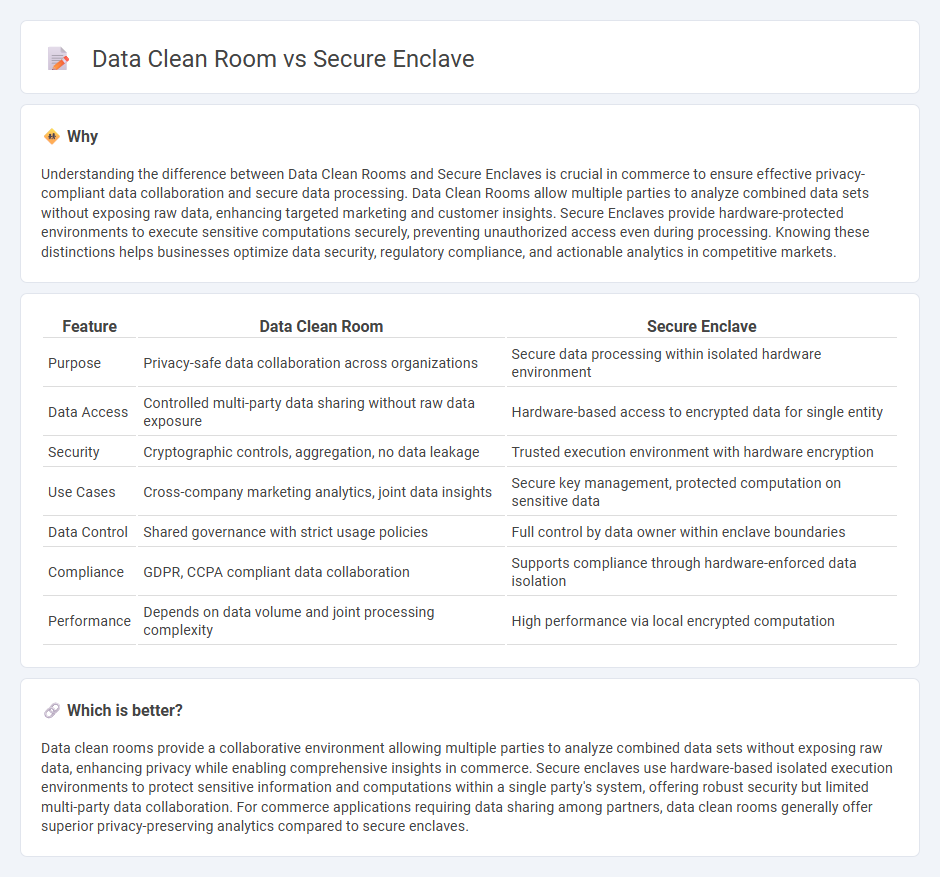
Understanding the difference between Data Clean Rooms and Secure Enclaves is crucial in commerce to ensure effective privacy-compliant data collaboration and secure data processing. Data Clean Rooms allow multiple parties to analyze combined data sets without exposing raw data, enhancing targeted marketing and customer insights. Secure Enclaves provide hardware-protected environments to execute sensitive computations securely, preventing unauthorized access even during processing. Knowing these distinctions helps businesses optimize data security, regulatory compliance, and actionable analytics in competitive markets.
Comparison Table
| Feature | Data Clean Room | Secure Enclave |
|---|---|---|
| Purpose | Privacy-safe data collaboration across organizations | Secure data processing within isolated hardware environment |
| Data Access | Controlled multi-party data sharing without raw data exposure | Hardware-based access to encrypted data for single entity |
| Security | Cryptographic controls, aggregation, no data leakage | Trusted execution environment with hardware encryption |
| Use Cases | Cross-company marketing analytics, joint data insights | Secure key management, protected computation on sensitive data |
| Data Control | Shared governance with strict usage policies | Full control by data owner within enclave boundaries |
| Compliance | GDPR, CCPA compliant data collaboration | Supports compliance through hardware-enforced data isolation |
| Performance | Depends on data volume and joint processing complexity | High performance via local encrypted computation |
Which is better?
Data clean rooms provide a collaborative environment allowing multiple parties to analyze combined data sets without exposing raw data, enhancing privacy while enabling comprehensive insights in commerce. Secure enclaves use hardware-based isolated execution environments to protect sensitive information and computations within a single party's system, offering robust security but limited multi-party data collaboration. For commerce applications requiring data sharing among partners, data clean rooms generally offer superior privacy-preserving analytics compared to secure enclaves.
Connection
Data clean rooms and Secure Enclaves both enhance data privacy and security in commerce by enabling safe data collaboration without exposing raw information. They utilize encrypted, isolated environments where businesses can share and analyze sensitive customer data while maintaining compliance with privacy regulations like GDPR and CCPA. Combining these technologies helps retailers and advertisers optimize marketing strategies through secure, privacy-preserving insights.
Key Terms
Encryption
Secure Enclaves provide hardware-based encryption that isolates data processing within a trusted execution environment, ensuring sensitive information remains encrypted and protected from external access. Data Clean Rooms leverage advanced cryptographic techniques like homomorphic encryption and secure multi-party computation to enable collaborative data analysis without exposing raw data. Explore the differences in encryption approaches to understand which solution best safeguards your data privacy.
Privacy-preserving analytics
Secure Enclave uses hardware-based isolation to protect sensitive data during processing, ensuring that analytics can be performed without exposing raw data to external systems. Data clean rooms create controlled environments where multiple parties collaborate on aggregated datasets without sharing personally identifiable information (PII), enhancing privacy in joint analytics. Explore deeper insights into how these technologies safeguard data privacy while enabling effective analytics.
Access control
Secure Enclaves provide hardware-isolated environments ensuring strict access control by encrypting data and limiting processing to authorized code only, effectively minimizing data exposure risks. Data Clean Rooms offer controlled, privacy-preserving environments where multiple parties can collaboratively analyze combined datasets without revealing underlying raw data, using strict access protocols and cryptographic techniques. Explore further to understand how these technologies safeguard sensitive information while enabling powerful data analytics.
Source and External Links
Secure Enclaves: The Powerful Way to Make Data ... - Secure enclaves, also called Trusted Execution Environments (TEE), are hardware-based isolated environments within CPUs that protect data and code running inside them from exposure even to the operating system or physical attackers, enabling confidential computing across many cloud platforms and servers.
Secure Enclave - Apple's Secure Enclave is a dedicated secure subsystem integrated into their SoCs across devices like iPhones, iPads, Macs, and others, isolated from the main processor to securely store and protect sensitive user data and cryptographic keys even if the main system is compromised.
What Is a Secure Enclave in WebAuthn? - Apple's Secure Enclave is a hardware-based key manager that isolates cryptographic operations from the main processor, specifically securing passkeys and WebAuthn credentials, and works only with specific cryptographic standards like NIST P-256 keys.
 dowidth.com
dowidth.com