Loss prevention analytics leverages data-driven techniques to detect patterns indicative of theft, fraud, or inventory shrinkage within retail operations. Suspicious transaction identification focuses on analyzing financial and behavioral signals to flag potentially fraudulent or unauthorized purchases in real time. Explore in-depth strategies to enhance retail security through cutting-edge loss prevention analytics and transaction monitoring methods.
Why it is important
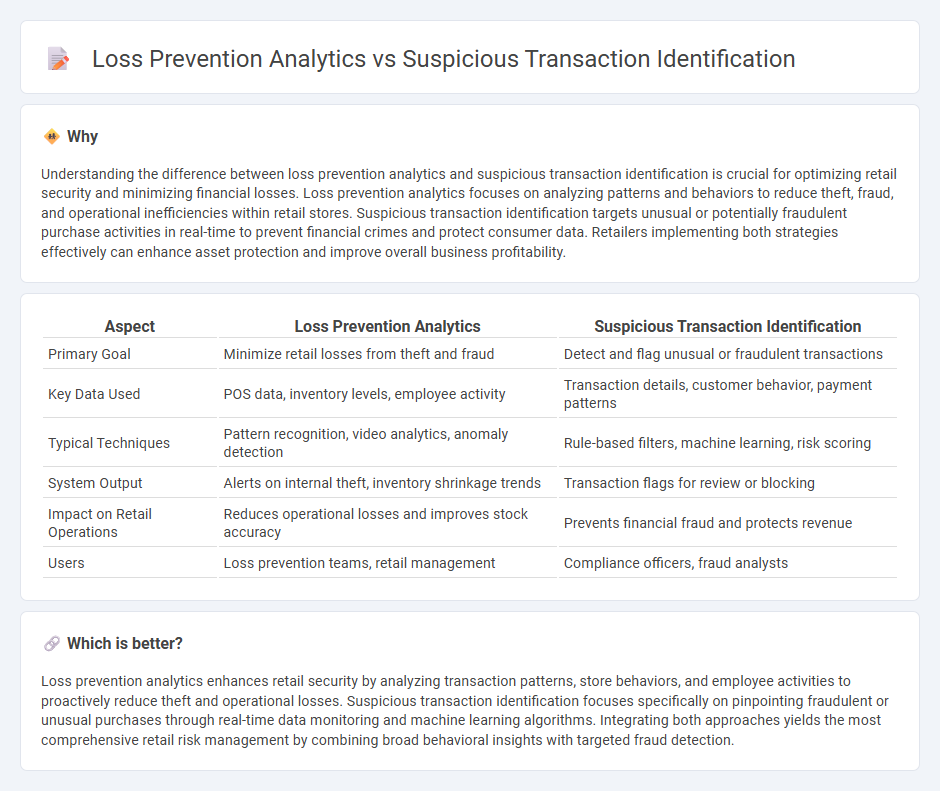
Understanding the difference between loss prevention analytics and suspicious transaction identification is crucial for optimizing retail security and minimizing financial losses. Loss prevention analytics focuses on analyzing patterns and behaviors to reduce theft, fraud, and operational inefficiencies within retail stores. Suspicious transaction identification targets unusual or potentially fraudulent purchase activities in real-time to prevent financial crimes and protect consumer data. Retailers implementing both strategies effectively can enhance asset protection and improve overall business profitability.
Comparison Table
| Aspect | Loss Prevention Analytics | Suspicious Transaction Identification |
|---|---|---|
| Primary Goal | Minimize retail losses from theft and fraud | Detect and flag unusual or fraudulent transactions |
| Key Data Used | POS data, inventory levels, employee activity | Transaction details, customer behavior, payment patterns |
| Typical Techniques | Pattern recognition, video analytics, anomaly detection | Rule-based filters, machine learning, risk scoring |
| System Output | Alerts on internal theft, inventory shrinkage trends | Transaction flags for review or blocking |
| Impact on Retail Operations | Reduces operational losses and improves stock accuracy | Prevents financial fraud and protects revenue |
| Users | Loss prevention teams, retail management | Compliance officers, fraud analysts |
Which is better?
Loss prevention analytics enhances retail security by analyzing transaction patterns, store behaviors, and employee activities to proactively reduce theft and operational losses. Suspicious transaction identification focuses specifically on pinpointing fraudulent or unusual purchases through real-time data monitoring and machine learning algorithms. Integrating both approaches yields the most comprehensive retail risk management by combining broad behavioral insights with targeted fraud detection.
Connection
Loss prevention analytics leverages data patterns and machine learning algorithms to detect anomalies indicative of theft or fraud in retail environments. Suspicious transaction identification is a critical component within this framework, focusing on flagging unusual purchase behaviors, transaction frequencies, or payment methods that deviate from established norms. Integrating these approaches enhances the accuracy of threat detection, reducing inventory shrinkage and financial losses for retailers.
Key Terms
**Suspicious transaction identification:**
Suspicious transaction identification employs advanced machine learning algorithms and pattern recognition techniques to detect anomalies and potentially fraudulent activities within financial data. This process prioritizes real-time monitoring of transactional behavior, flagging transactions that deviate from established norms to mitigate risks before losses occur. Explore the latest methods in suspicious transaction identification to enhance your fraud detection strategies.
Anomaly detection
Suspicious transaction identification relies heavily on anomaly detection techniques to flag unusual patterns that may indicate fraud or money laundering activities. Loss prevention analytics uses anomaly detection to pinpoint deviations in transactional data that could signal theft, errors, or operational inefficiencies within retail environments. Explore advanced anomaly detection methods for a deeper understanding of their impact on financial security and operational integrity.
Fraud patterns
Suspicious transaction identification leverages machine learning algorithms to detect anomalies and patterns indicative of fraud across financial operations, enhancing real-time response capabilities. Loss prevention analytics integrates data from multiple sources such as point-of-sale systems, customer behavior, and historical fraud cases to predict potential losses and optimize security measures. Explore advanced fraud pattern detection techniques to safeguard your business more effectively.
Source and External Links
Step-by-Step Guide to Investigating Suspicious Transactions - Suspicious transaction identification involves recognizing red flags like unusual transaction size or frequency, geographic anomalies, inconsistent activities, complex patterns, and anonymous methods, which require contextual expert judgment for further investigation.
Identifying Suspicious Transactions in Money Laundering - Tookitaki - Suspicious transactions deviate from normal behavior and include indicators such as unusually large amounts, complex structures, frequent transfers, and lack of customer due diligence, serving as alerts for money laundering risks.
Suspicious transactions identified by your transaction monitoring systems - Effective transaction monitoring systems must alert unusual, large, or complex transactions, including those mismatching customer profiles, involving rapid transfers, using third parties, or linked to high-risk assets and countries, to help detect potential money laundering or terrorism financing.
 dowidth.com
dowidth.com