Data clean rooms enable multiple parties to securely analyze and share aggregated commerce data without exposing individual customer information, enhancing privacy compliance. Homomorphic encryption allows computations on encrypted commercial datasets, preserving data confidentiality while delivering actionable insights. Explore the differences and applications of these technologies in commerce data security.
Why it is important
Understanding the difference between data clean rooms and homomorphic encryption is crucial for secure commerce as data clean rooms enable multiple parties to collaboratively analyze encrypted data without sharing raw information, enhancing privacy compliance during transactions. Homomorphic encryption allows computations on encrypted data without decryption, ensuring end-to-end data confidentiality in financial operations. Knowing these distinctions helps businesses implement the right technology for secure data sharing, risk management, and regulatory adherence in the commercial ecosystem. Proper selection between these methods optimizes secure data collaboration and drives trust in digital commerce.
Comparison Table
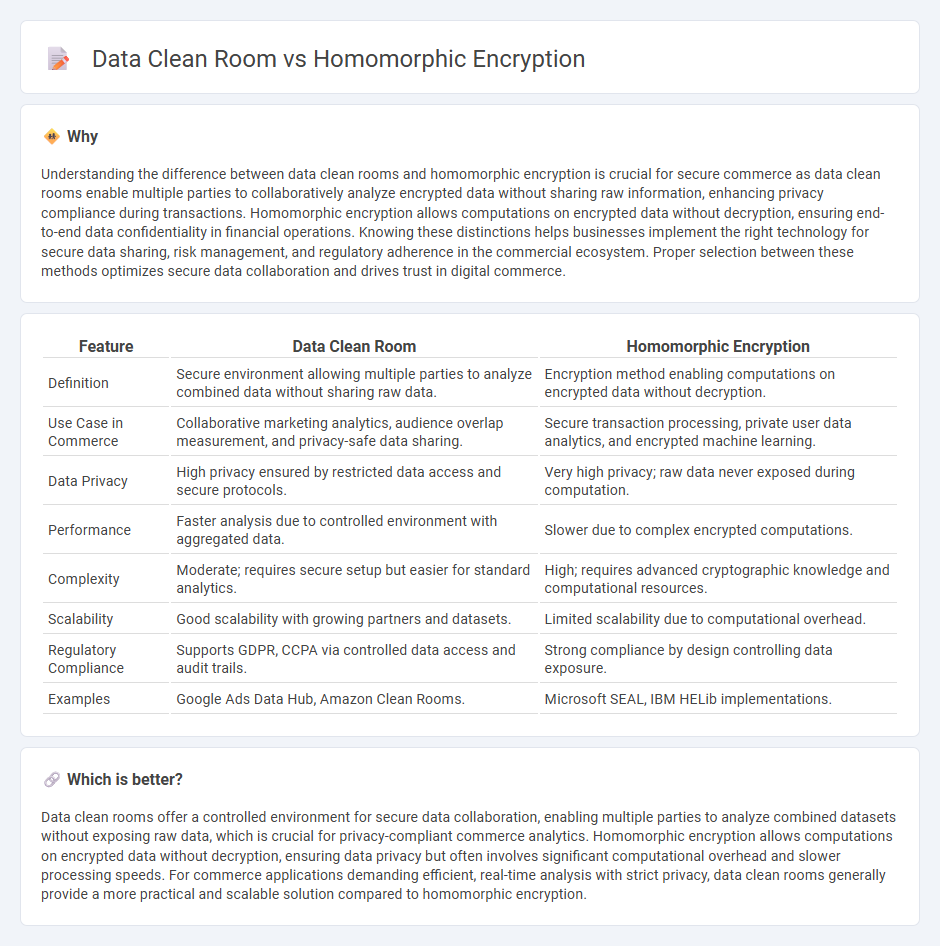
| Feature | Data Clean Room | Homomorphic Encryption |
|---|---|---|
| Definition | Secure environment allowing multiple parties to analyze combined data without sharing raw data. | Encryption method enabling computations on encrypted data without decryption. |
| Use Case in Commerce | Collaborative marketing analytics, audience overlap measurement, and privacy-safe data sharing. | Secure transaction processing, private user data analytics, and encrypted machine learning. |
| Data Privacy | High privacy ensured by restricted data access and secure protocols. | Very high privacy; raw data never exposed during computation. |
| Performance | Faster analysis due to controlled environment with aggregated data. | Slower due to complex encrypted computations. |
| Complexity | Moderate; requires secure setup but easier for standard analytics. | High; requires advanced cryptographic knowledge and computational resources. |
| Scalability | Good scalability with growing partners and datasets. | Limited scalability due to computational overhead. |
| Regulatory Compliance | Supports GDPR, CCPA via controlled data access and audit trails. | Strong compliance by design controlling data exposure. |
| Examples | Google Ads Data Hub, Amazon Clean Rooms. | Microsoft SEAL, IBM HELib implementations. |
Which is better?
Data clean rooms offer a controlled environment for secure data collaboration, enabling multiple parties to analyze combined datasets without exposing raw data, which is crucial for privacy-compliant commerce analytics. Homomorphic encryption allows computations on encrypted data without decryption, ensuring data privacy but often involves significant computational overhead and slower processing speeds. For commerce applications demanding efficient, real-time analysis with strict privacy, data clean rooms generally provide a more practical and scalable solution compared to homomorphic encryption.
Connection
Data clean rooms and homomorphic encryption intersect in secure data collaboration by enabling multiple parties to analyze combined datasets without exposing raw data. Homomorphic encryption allows computations on encrypted data, preserving privacy while data clean rooms provide controlled environments for joint analytics. This synergy enhances data privacy compliance and fosters trust in commerce-driven data partnerships.
Key Terms
Privacy-preserving computation
Homomorphic encryption enables computations on encrypted data without needing decryption, preserving privacy throughout data processing, while data clean rooms provide a controlled environment where multiple parties can collaboratively analyze data under strict access policies. Both techniques improve privacy-preserving computation but differ in implementation: homomorphic encryption secures data mathematically, and clean rooms enforce privacy through operational governance. Explore the nuances and applications of these advanced privacy-preserving methods for more insights.
Secure multiparty analysis
Homomorphic encryption enables secure multiparty analysis by allowing computations on encrypted data without revealing the underlying information, ensuring privacy throughout the process. Data clean rooms provide controlled environments where multiple parties can collaboratively analyze combined datasets under strict privacy and compliance protocols. Explore the nuances and applications of these privacy-enhancing technologies to optimize secure multiparty analysis.
Encrypted data collaboration
Homomorphic encryption enables processing encrypted data without decrypting it, preserving privacy while allowing complex computations on sensitive information. Data clean rooms provide a secure environment where multiple parties share and analyze aggregated data without exposing raw data, ensuring compliance and protection. Explore how these advanced technologies revolutionize encrypted data collaboration for enhanced security and compliance.
Source and External Links
Homomorphic encryption - Wikipedia - Homomorphic encryption allows computation on encrypted data without decrypting it first, enabling results to remain encrypted, with several types ranging from partially to fully homomorphic encryption that vary in their computational abilities and complexity.
What is homomorphic encryption, and why isn't it mainstream? - Keyfactor - Homomorphic encryption is an encryption method that permits mathematical operations on encrypted data, maintaining strong security while enabling computation over data in use, which is challenging due to the relationship needed between plaintext and ciphertext.
What Is Homomorphic Encryption? - Chainlink - Homomorphic encryption schemes include partially, somewhat, leveled fully, and fully homomorphic encryption, with increasing capabilities that allow encrypted data to be processed for applications such as machine learning and multi-party computation, albeit with trade-offs in computational cost and complexity.
 dowidth.com
dowidth.com